What Steps are Taken by Synology to Improve Data Security?
With increase in cybercrimes, data security has been one of the major concerns these days. According to a study, about 44% of organizations’ data get breached by cybercriminals globally. With that said, what we think in the first case is incident response.
Yes, it is important to have an incident response plan. But, that does not reduce the importance of prioritizing the software security so that such cybercrimes do not happen. This brings the Security Development Lifecycle (SDL) in light. SDL is a common practice that mitigates the security risk as per the requirements. In simple words, the main aim of SDL is to build a highly secure product.
How Does Synology Improve Data Security?
Synology is trusted by many when it comes to storage and networking devices. This automatically increases the user’s expectation of getting a top-notch security performance from a Synology device. Synology has crafted a 4-phase software development process so that product’s safety can be ensured. The four phases of the process are mentioned below:
- Design
- Development
- Verification
- Release
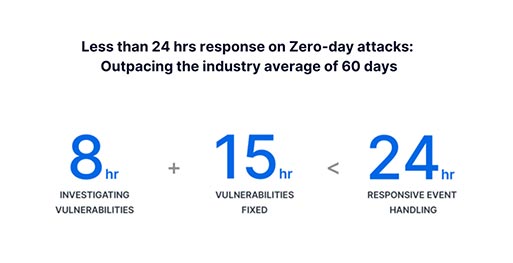
These 4 steps are carried out very safely so that the final product comes out with the highest security level. On the off-chance, security vulnerability occurs, Synology promises to fix it in 24 hours which is still 60 days in the industry. No security exploits have been noticed by Synology according to a catalog by Cybersecurity and Infrastructure Security Agency introduced in 2k21.
Now, let us move ahead and discuss how Synology crafts its products so that security levels can be taken care of:
Synology NAS and Data Security
1. The Design Phase: Whenever a new Synology product or service/feature is proposed, the Product Security Assurance Program is initiated. Teams collaborate to review the infrastructure and design to address areas of improvement. This can be understood with the example of DSM 7.0 in which root privilege was removed and granted minimum permissions to users to reduce security risks. The company also introduced Synology two factor authentication to increase the security level.
2. The Development Phase: The development phase starts when the product specifications are confirmed. In order to ensure the quality of the product from the beginning, Synology uses automatic tools to rule out the possible vulnerabilities and defects. Thereafter, Dynamic Analysis Security Testing is done to notice the changes in the code and all functionality is tested on the app thereby reducing security threats.
3. The Verification Phase: This phase considers the attacker’s mindset. Synology introduced the Synology Red Team in 2022. This team consists of hackers having professional experience who examine the product from the point of view of a hacker to identify security threats and rule them out. The team has already identified 21% of system bugs and addressed them effectively.
4. The Release Phase: The Synology Red team identifies threats and security issues and the Synology Blue team plays defense. It means they do the exact opposite of the red team. The Blue team addresses the security issues. The team initiates an assessment to identify the impact within 8 hours. After the issue is identified, vulnerability is fixed in 24 hours which is much less than the industry average of 60 days of mean time.
The Conclusion
Synology strives to provide the best experience to its users. That is why, R&D team at Synology works to improve the security and performance of the manufactured devices.